This interview preparation guide will discuss some commonly asked Spring Security interview questions. Whether you’re preparing for a job interview or simply looking to enhance your knowledge of Spring Security, these questions will help you understand key concepts and guide in designing solutions to the common security problems.
Interview Questions on Core Concepts
1. What are the core features of Spring Security?
The two most prominent features offered by Spring Security are authentication and authorization. These features play a crucial role in ensuring the security of an application. However, Spring Security goes beyond authentication and authorization and offers additional capabilities to protect against exploits and integrate with other frameworks.
1.1. Authentication
Authentication is the process of validating the identity of a user who is attempting to access the application. Spring Security provides multiple authentication methodologies (form-based authentication, HTTP basic authentication, OAuth2, Siteminder, OpenID Connect, LDAP, JDBC, etc), allowing an application to authenticate users using various approaches.
It also supports customization, enabling the implementation of custom authentication mechanisms when the default options do not meet the requirements.
1.2. Authorization
Authorization is the process of granting permissions or rights to authenticated users or entities. Once a user or entity is successfully authenticated, authorization determines what actions or resources they are allowed to access within an application. Spring Security provides developers with various approaches to implement authorization and control user access to different parts of an application. Here are some of the common approaches:
- Web URL-based Authorization: Access control can be enforced based on specific URLs or URL patterns, regulating which users can access certain resources.
- Method-level Authorization: Even methods within Java Beans can be access-controlled if required, providing fine-grained authorization at the method level.
- Domain Instance-level Authorization: Spring Security offers the ability to control access to specific domain instances, allowing authorization based on the ownership or association of certain entities.
1.3. Protection Against Exploits
Spring Security provides several features to protect against common web application security vulnerabilities. Some of the notable features include:
- Cross-Site Request Forgery (CSRF) protection: Spring Security automatically adds CSRF tokens to forms and AJAX requests, preventing CSRF attacks.
- Cross-Site Scripting (XSS) protection: Spring Security supports output encoding and provides utilities to prevent XSS attacks by sanitizing user input.
- Click-jacking protection: Spring Security includes X-Frame-Options support to prevent click-jacking attacks.
1.4. Integrations
Spring Security seamlessly integrates with other frameworks and libraries to enhance the security of the applications. Some key integrations are:
- Spring MVC: Spring Security integrates with Spring MVC to provide seamless security features for web applications. It enables the secure handling of requests, authentication, authorization, and protection against common web vulnerabilities.
- Spring Data: Spring Security integrates with Spring Data to enable referring to the current user within queries. This integration ensures that user-specific data can be easily accessed and filtered based on authentication and authorization rules.
- Jackson: Jackson‘s support enables efficient serialization and deserialization of Spring Security-related classes, particularly when working with distributed sessions or frameworks like Spring Session, resulting in improved efficiency and scalability.
- Cryptography: Spring Security integrates with various cryptographic libraries and algorithms to provide secure storage and transmission of sensitive information. This integration includes features like password hashing, encryption, and secure communication protocols to protect data confidentiality and integrity.
For more detailed information on Spring Security features, refer to the official documentation.
2. Explain the core components of Spring Security?
When it comes to Spring Security, several core components play a vital role in providing security features for Java applications. These components work together to ensure robust authentication, authorization, and other security functionalities.
2.1. DelegatingFilterProxy
The DelegatingFilterProxy is a special Servlet Filter provided by Spring Framework. It acts as an entry point for handling security-related requests. When a request is received, the DelegatingFilterProxy delegates the request to the Spring FilterChainProxy bean for further processing(springSecurityFilterChain bean). The FilterChainProxy utilizes the SecurityFilterChain to determine the appropriate set of filters to be invoked for the current request.
2.2. FilterChainProxy
The FilterChainProxy determines which filters to apply based on the incoming request’s URL pattern and the defined security configuration. It evaluates the request against the configured security rules and selects the appropriate filter chain ( using @EnableWebSecurity, the FilterChainProxy is automatically created as a bean. It wraps the actual security filter chain and acts as a delegate for handling requests).
2.3. SecurityFilterChain
When a request is received, the FilterChainProxy locates the corresponding SecurityFilterChain and executes the list of filters within that chain. Each filter performs its designated task based on the security configuration of the application. The filters may modify the request, perform authentication checks, validate permissions, or handle session-related operations.
Some important security filters in Spring Security include:
- UsernamePasswordAuthenticationFilter: This filter handles form-based authentication by intercepting login requests and authenticating users based on their provided credentials.
- BasicAuthenticationFilter: This filter handles Basic Authentication, where users provide credentials in the form of a username and password in the HTTP headers.
- RememberMeAuthenticationFilter: This filter enables the Remember-Me functionality, allowing users to log in automatically using a persistent token stored in a cookie.
- LogoutFilter: This filter handles the logout process, invalidating the user session, clearing authentication details, and performing additional actions such as redirecting to a specific logout page.
- ExceptionTranslationFilter: This filter catches any authentication or access-related exceptions thrown during request processing and translates them into meaningful responses, such as redirecting to a login page or returning a forbidden response.
Once the request reaches registered filters inside the SecurityFilterChain, the corresponding filters delegate the request to other beans for performing corresponding tasks. For example, AuthenticationProcessingFilter prepares the Authentication instance and delegates it to AuthenticationManager for authentication flow.

2.4. AuthenticationManger
The AuthenticationManager is responsible for authenticating users. It has a single method called authenticate(), which takes an instance of Authentication as a parameter. The authenticate() method is responsible for validating the provided credentials (with the help of an appropriate implementation of AuthenticationProvider) and returning an authenticated Authentication object if the authentication is successful.
Spring Security, by default, provides an implementation of the AuthenticationManager interface called ProviderManager. The ProviderManager delegates the authentication process to a list of AuthenticationProvider instances.
2.5. AuthenticationProvider
The AuthenticationProvider is responsible for authenticating a specific type of credentials or authentication mechanism. It defines the contract for performing authentication against a particular source, such as a user database, external authentication service, or any other custom authentication mechanism.
When multiple authentication mechanisms are used within an application, multiple AuthenticationProvider instances can be configured to handle each mechanism separately.
For more information, please refer to the official documentation.
3. How does Spring Security handle user authentication?
At a high level, Spring Security handles user authentication through a series of steps. Most steps are common for all kinds of authentications, yet few authentication flows require specific steps.
The following steps demonstrate the form-login-based authentication where the user inputs the username/password combination in the request.
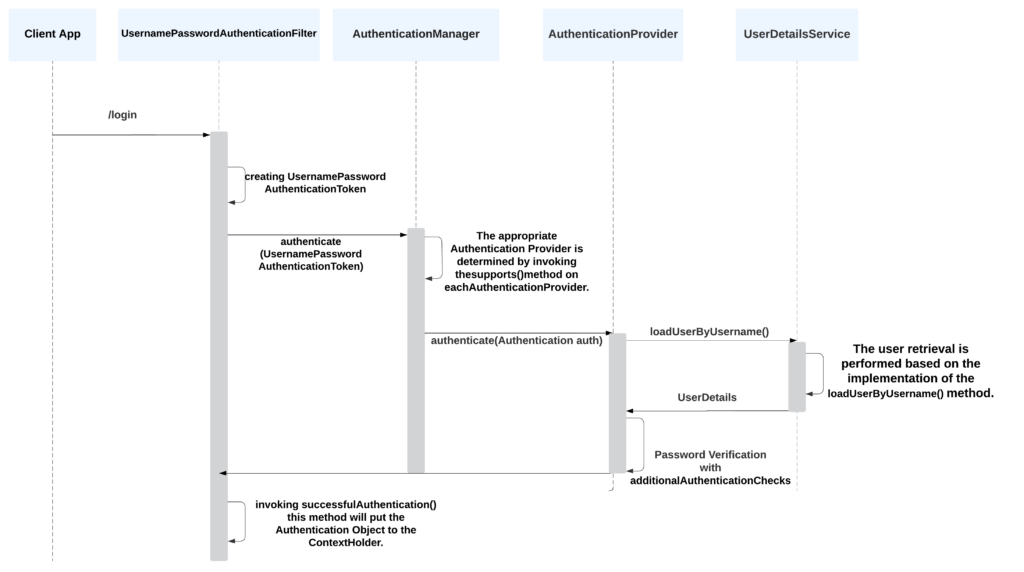
- The user attempts to access a secured resource or initiates a login request, the request is intercepted by Spring Security which will redirect us to the login page.
- The Authentication Filter UsernamePasswordAuthenticationFilter, is responsible for capturing the user’s credentials from the request (typically UsernamePasswordAuthenticationFilter is called for every request made to /login).
- UsernamePasswordAuthenticationFilter extracts the username and password and creates an Authentication object (instance from UsernamePasswordAuthenticationToken ).
- The Authentication object is then passed to the AuthenticationManager.
- The AuthenticationManager delegates the authentication process to one or more AuthenticationProvider.
- AuthenticationProvider verifies the credentials using a UserDetailsService bean that has the method
loadUserByUsername(username). It returnsUserDetailsobject that contains user data. If no user is found with the given username,UsernameNotFoundExceptionis thrown. - If the authentication is successful, the Authentication object, now containing the authenticated user’s information, is returned to the AuthenticationManager.
- The AuthenticationManager stores the authenticated Authentication object in the SecurityContext.
- The Security Context is typically stored in a thread-local variable, making it accessible throughout the application.
- With the user authenticated, Spring Security allows the user to access the requested resource or proceed with the requested action.
4. How does the AuthenticationManager determine the appropriate AuthenticationProvider?
During the authentication process, the AuthenticationManager receives an Authentication object representing the user’s credentials. The AuthenticationManager loops through each AuthenticationProvider and calls their supports(Class<?> authentication) method to determine if the provider supports the specific type of Authentication object. Each AuthenticationProvider implements this method and typically checks if the provider can handle the authentication request based on the authentication object’s class.
This is a code snippet from the source code of ProviderManager, which is the default implementation of AuthenticationManager:
public Authentication authenticate(Authentication authentication) throws AuthenticationException {
Class<? extends Authentication> toTest = authentication.getClass();
// .......
for (AuthenticationProvider provider : getProviders()) {
if (!provider.supports(toTest)) {
continue;
}
// ......
}Once an AuthenticationProvider that supports the given authentication object is found, the AuthenticationManager calls the provider’s authenticate(Authentication authentication) method. This method performs the authentication logic specific to that provider, such as validating the credentials against a user database or an external authentication service.
5. How does Spring Security handle user authorization?
At a high level, Spring Security handles user authorization through a process that involves several components working together.
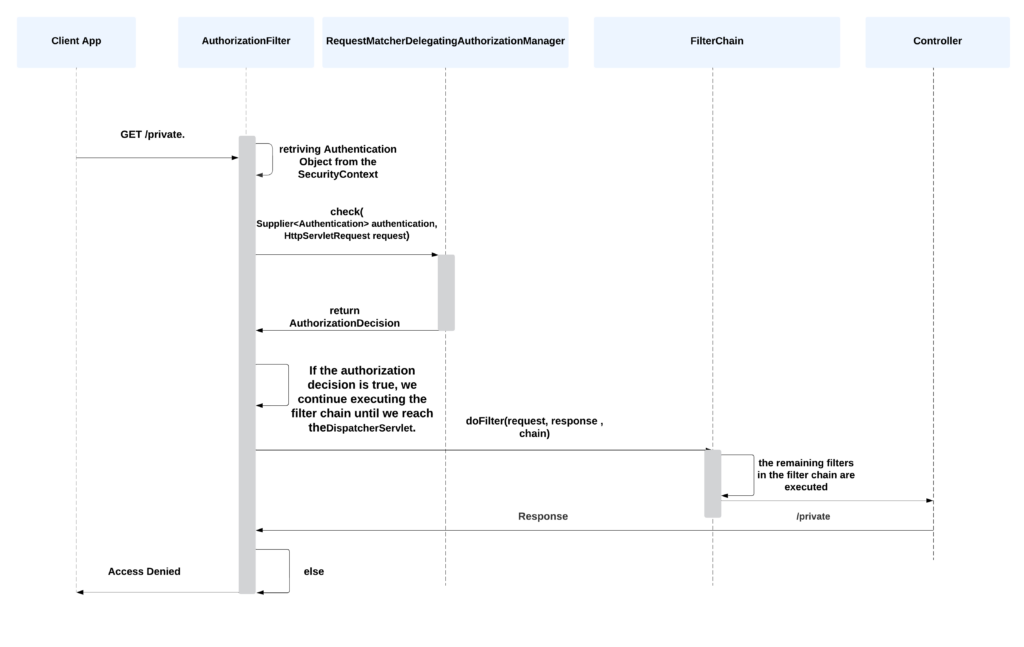
Here’s an overview of the process.
- Once the request is authenticated, it proceeds to the authorization phase. The FilterChainProxy invokes the appropriate authorization filter in the filter chain.
- The AuthorizationFilter retrieves the Authentication object from the SecurityContextHolder. It then delegates the authorization process to the AuthorizationManager, which is responsible for making the final authorization decision based on the configured access control rules and permissions. The AuthorizationManager supersedes both the AccessDecisionManager and AccessDecisionVoter.
- The AuthorizationFilter constructs a Supplier object using the Authentication object and the HTTP request. This Supplier is then passed to the
check() method of the RequestMatcherDelegatingAuthorizationManager, which is the default AuthorizationManager used by Spring Security. - The RequestMatcherDelegatingAuthorizationManager evaluates the supplied
Supplieragainst the configuredRequestMatcherinstances to determine if the requested resource matches any of the specified access control rules. - The
checkmethod of the RequestMatcherDelegatingAuthorizationManager returns an AuthorizationDecision object. If the authorization decision isfalse, indicating that access is denied, an exception is thrown (typically a403 Access Deniedexception). - On the other hand, if the authorization decision is
true, indicating that access is granted, the filter chain continues to execute until it reaches the DispatcherServlet. Each filter in the chain performs its designated tasks, such as request preprocessing, security checks, or any other custom functionality.
6. What is PasswordEncoder? What is the default encoder?
The PasswordEncoder is an interface used for encoding and verifying passwords using methods encode() & matches(). It is responsible for taking a user’s password, applying a one-way hashing algorithm, and securely storing the hashed password. When a user attempts to log in, the entered password is again hashed using the same algorithm, and the generated hash is compared with the stored hashed password for authentication.
The default password encoder is BCryptPasswordEncoder. BCrypt is a widely used and secure hashing algorithm that incorporates salting and cost factors to protect against various types of attacks, including brute-force attacks. The BCryptPasswordEncoder is a good choice for password storage as it provides a high level of security.
@Bean
public PasswordEncoder passwordEncoder() {
return new BCryptPasswordEncoder();
}For custom requirements, we can configure a custom password encoder as well.
Implement the PasswordEncoder interface
Create a class that implements the PasswordEncoder interface. This class will provide the implementation for encoding and verifying passwords.
public class CustomPasswordEncoder implements PasswordEncoder {
@Override
public String encode(CharSequence rawPassword)
// Implement your password encoding logic here
// Return the encoded password as a String
}
@Override
public boolean matches(CharSequence rawPassword, String encodedPassword) {
// Implement your password verification logic here
// Compare the rawPassword with the encodedPassword and return true or false
}
}Configure CustomPasswordEncoder
In our Spring Security configuration, we can specify the use of our custom password encoder by defining a PasswordEncoder bean. Spring Security will use this bean for password encoding and verification.
@Configuration
@EnableWebSecurity
public class SecurityConfig {
@Bean
public PasswordEncoder passwordEncoder() {
return new CustomPasswordEncoder();
}
// Other security configuration code
}Interview Questions on Implementing Spring Security
7. How to enable Spring security in a non-Spring boot application?
When it comes to enabling Spring Security in a non-Spring Boot application, there are a few approaches we can take. Let’s explore two standard methods:
- Java-based configuration
- XML-based configuration
Java-based Configuration With AbstractSecurityWebApplicationInitializer
In Java configuration, we can enable Spring Security by extending the AbstractSecurityWebApplicationInitializer class and optionally overriding its methods to configure the DelegatingFilterProxy and associate it with the springSecurityFilterChain bean. It avoids writing servlet-filter configurations in web.xml file.
We can define the custom security beans in the SecurityConfig.java.
public class SpringSecurityInitializer extends AbstractSecurityWebApplicationInitializer {
public SpringSecurityInitializer() {
super(SecurityConfig.class);
}
}XML Based Configuration
In XML configuration, we need to explicitly define the DelegatingFilterProxy bean and map it to the springSecurityFilterChain bean using the filter name. This linkage is typically done in the web.xml file:
<filter>
<filter-name>springSecurityFilterChain</filter-name>
<filter-class>org.springframework.web.filter.DelegatingFilterProxy</filter-class>
</filter>
<filter-mapping>
<filter-name>springSecurityFilterChain</filter-name>
<url-pattern>/*</url-pattern>
<dispatcher>ERROR</dispatcher>
<dispatcher>REQUEST</dispatcher>
</filter-mapping>8. How to enable Spring security in a Spring boot application?
If we are using Spring Boot, enabling Spring Security is quite straightforward. All we need to do is add the Spring Security starter to our project’s dependencies, and the auto-configuration will be available by default. This is because when Spring Security is in the classpath, the WebSecurityEnablerConfiguration automatically activates the @EnableWebSecurity annotation for us.
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>9. What is the purpose of the @EnableWebSecurity in Spring Security?
The @EnableWebSecurity annotation is used to enable the web security of an application. When this annotation is added to a configuration class, it indicates that the class will provide the necessary configurations and settings for securing the web application.
In a non-Spring boot application, the @EnableWebSecurity annotation performs the following tasks implicitly, other than providing custom configuration beans written by developers.
- Creates a Spring Security filter chain: It initializes and configures the filter chain responsible for processing incoming requests and applying security measures.
- Configures the security context: It sets up the security context for handling authentication and authorization. The security context holds information about the currently authenticated user and their granted authorities.
In Spring boot application, using the @EnableWebSecurity annotation is optional. Spring boot security auto-configuration provides almost the same features as using the @EnableWebSecurity annotation.
When @EnableWebSecurity is used in a Spring boot application, the default autoconfiguration backs off and provided configuration takes precedence.
@Configuration
@EnableWebSecurity
public class SecurityConfig {
@Bean
public WebSecurityCustomizer webSecurityCustomizer() {
return (web) -> web.ignoring()
.requestMatchers("/resources/**");
}
@Bean
public SecurityFilterChain securityFilterChain(HttpSecurity http) throws Exception {
http.authorizeHttpRequests()
.requestMatchers("/public/**").permitAll()
.anyRequest().hasRole("USER")
.and()
.formLogin().permitAll();
return http.build();
}
// Possibly more bean methods ...
}10. What is the difference between Role and Authority in Spring Security?
In Spring Security, both roles and authorities are used to define and manage user permissions. However, there is a subtle difference between the two:
- Role: A role represents a broad category or group of permissions. It is typically used to group related authorities together. Roles can be assigned to users, and users can have multiple roles. For example, roles can be “ADMIN”, “USER”, or “MANAGER”. Roles are often used for high-level access control decisions.
- Authority: An authority, also known as permission or privilege, represents a specific permission that a user can possess. It defines a fine-grained level of access control. Authorities are granted to users either directly or through roles. For example, authorities can be “READ_DATA”, “WRITE_DATA”, or “DELETE_DATA”. Authorities are used for precise access control decisions.
11. How to implement method security using annotations?
In addition to URL-level security, Spring Security also supports security at the method level. To implement the method-level security using annotations in Spring Security, we can annotate any @Configuration class with @EnableMethodSecurity.
@Configuration
@EnableWebSecurity
@EnableMethodSecurity
public class SecurityConfig {
//..
}Now we can @Secured, @PreAuthorize, @PostAuthorize, @PreFilter, and @PostFilter annotations to authorize method invocations, including the input parameters and return values.
In the following example, the deleteProduct method is secured with the @PreAuthorize annotation, and the expression hasRole('ADMIN') ensures that only users with the “ADMIN” role can invoke this method.
@PreAuthorize("hasRole('ADMIN')")
public void deleteProduct(Long productId) {
// Method logic for deleting a product
}By default, method security is disabled in Spring boot.
Interview Questions on Advance Configurations
12. What is Basic Authentication? How to implement it?
Basic Authentication is a simple authentication mechanism in which the client includes the username and password in the HTTP headers of each request (the credentials are sent in the format ‘username:password‘, which is then Base64-encoded before being included in the Authorization header). The server then validates the credentials and grants access to the requested resource if they are correct.
To enable basic-authentication in Spring Security, we use the httpBasic() method.
@Bean
public SecurityFilterChain securityFilterChain (HttpSecurity http) throws Exception {
http.authorizeHttpRequests()
.anyRequest().authenticated()
.and()
.httpBasic();
return http.build();
}13. What is JWT Authentication? How to implement it?
JWT (JSON Web Token) authentication is a popular authentication mechanism that uses JSON-based tokens for securely transmitting authentication and authorization information between parties. It enables stateless authentication and eliminates the need for session storage on the server side.
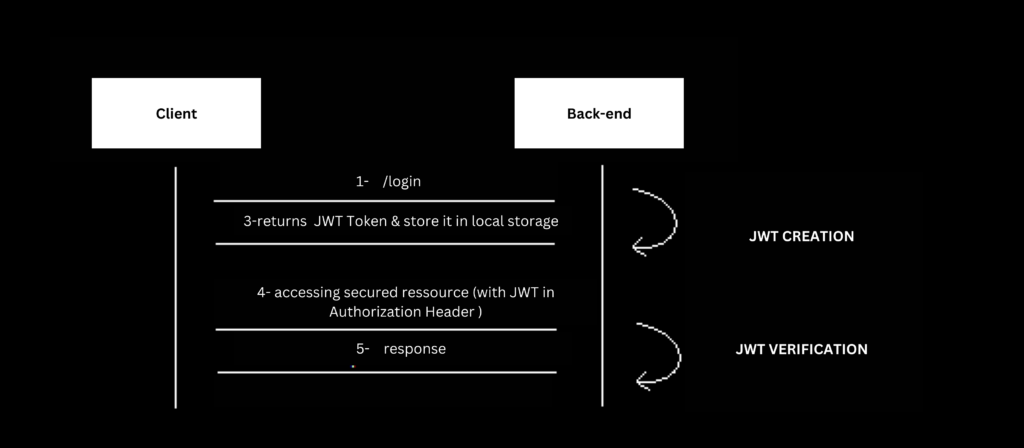
To implement JWT authentication in Spring Security, we can follow these steps:
- Include the necessary dependencies:
spring-security-jwtand a library for JWT processing (e.g.,jjwt). - Implement a JWT token provider: Create a class responsible for generating JWT tokens. This class should include methods for creating and signing JWTs, setting the claims, and specifying the expiration time.
- Implement JWT authentication filter: Create a custom filter that intercepts incoming requests, extracts the JWT token from the request header, and validates it. This filter should use the JWT token provider to validate the token’s signature and extract the necessary user details.
- Configure JWT authentication filter with Spring Security: we should configure the JWT authentication filter to be used for processing authentication requests
- Implement user details service: Create a user details service that retrieves the user’s details based on the information stored in the JWT token. This service is responsible for fetching user details from a user repository or any other data source.
For more information on the implementation details, read the article JWT authentication in Spring Security.
14. How to implement OAuth2 Security?
OAuth2 is an authorization framework that allows applications to obtain limited access to user accounts. It involves multiple components, including the authorization server and resource server. The authorization server handles authentication and issues access tokens, while the resource server hosts protected resources and verifies access tokens.
To implement OAuth2 security, you’ll need to configure both, authorization and resource servers.
Authorization Server
The authorization server is responsible for authenticating users and issuing access tokens. In Spring Security, we can configure the authorization server using the AuthorizationServerConfigurerAdapter class.
The following class sets up an authorization server, defines the security constraints, and configures the clients that can access the server to obtain access tokens for authentication and authorization purposes.
@Configuration
@EnableAuthorizationServer
public class OAuth2AuthorizationServer extends AuthorizationServerConfigurerAdapter {
@Autowired
private BCryptPasswordEncoder passwordEncoder;
@Override
public void configure(AuthorizationServerSecurityConfigurer security) throws Exception {
security
.tokenKeyAccess("permitAll()")
.checkTokenAccess("isAuthenticated()");
.allowFormAuthenticationForClients();
}
@Override
public void configure(ClientDetailsServiceConfigurer clients) throws Exception {
clients.inMemory()
.withClient("client-id")
.secret("client-secret")
.authorizedGrantTypes("authorization_code", "password", "refresh_token")
.scopes("read", "write")
.accessTokenValiditySeconds(3600)
.refreshTokenValiditySeconds(86400);
}
}Resource Server
The resource server hosts protected resources and verify access tokens. In Spring Security, we can configure the resource server using the ResourceServerConfigurerAdapter class.
In the following example, OAuth2ResourceServerConfig configures the resource server by specifying the access rules for different API endpoints. It allows unrestricted access to public resources while requiring authentication for private access.
@Configuration
@EnableResourceServer
public class OAuth2ResourceServerConfig extends ResourceServerConfigurerAdapter {
@Override
public void configure(HttpSecurity http) throws Exception {
http.authorizeRequests()
.antMatchers("/api/public/**").permitAll()
.antMatchers("/api/private/**").authenticated();
}
}The resource server needs to validate the access token to ensure it is issued by a trusted authorization server and has not expired or been tampered with.
One common approach is to use the RemoteTokenServices class provided by Spring Security. The resource server requests to the authorization server’s /oauth/check_token endpoint, passing the access token as a parameter.
@Bean
public ResourceServerTokenServices tokenService() {
RemoteTokenServices tokenServices = new RemoteTokenServices();
tokenServices.setClientId("client-id");
tokenServices.setClientSecret("client-secret");
tokenServices.setCheckTokenEndpointUrl("http://localhost:8080/oauth/check_token");
return tokenServices;
}15. What is CSRF protection in Spring Security? How to implement it?
CSRF (Cross-Site Request Forgery) protection is a security mechanism that prevents attackers from exploiting the trust between a user and a website. It guards against CSRF attacks, where an attacker tricks a user’s browser into performing unwanted actions on a website without the user’s knowledge or consent.
To implement CSRF protection in Spring Security, we can follow these steps:
- In your client-side code (typically in HTML forms), include the CSRF token as a hidden field or a request header when making requests to your application’s endpoints.
- On the server side, configure Spring Security to expect and validate the CSRF token in incoming requests.
By default, Spring Security automatically enables CSRF protection. It adds a CSRF token to forms and includes it in subsequent requests.
We can configure/customize CSRF protection in Spring Security using the csrf() method.
@Configuration
public class SecurityWithCsrfCookieConfig {
@Bean
public SecurityFilterChain filterChain(HttpSecurity http) throws Exception {
http
.csrf()
.csrfTokenRepository(CookieCsrfTokenRepository.withHttpOnlyFalse());
return http.build();
}
}In the above example, we configure CSRF protection to use the CookieCsrfTokenRepository and ensure that the CSRF token is accessible to JavaScript by setting withHttpOnlyFalse(). we can choose a different CsrfTokenRepository implementations based on our requirements.
16. What is CORS and how is it handled in Spring Security?
CORS (Cross-Origin Resource Sharing) is a security mechanism enforced by web browsers to restrict cross-origin HTTP requests. It allows servers to specify which origins (domains) are allowed to access their resources.
In Spring Security, there are two methods to configure CORS in our applications:
Global Configuration
We can configure the CORS support, globally, by creating a bean of the CorsConfigurationSource class. In this example, we are configuring the CORS policy to allow cross-origin requests from the specified origin, which is http://localhost:8081 in this case.
@Bean
public CorsConfigurationSource corsConfigurationSource() {
CorsConfiguration config = new CorsConfiguration();
config.setAllowCredentials(true);
config.addAllowedHeader("*");
config.addAllowedMethod("*");
config.addAllowedOrigin("http://localhost:8081");
UrlBasedCorsConfigurationSource source = new UrlBasedCorsConfigurationSource();
source.registerCorsConfiguration("/**", config);
return source;
}Handler Method-Specific Configuration
If we only need CORS for specific endpoints, we can use the @CrossOrigin annotation at the method level. This allows us to specify the allowed source, HTTP methods, and other configurations.
In this example, the /api/resource endpoint allows cross-origin requests only from http://example.com using the specified HTTP methods.
@RestController
public class MyController {
@GetMapping("/api/resource")
@CrossOrigin(origins = "http://example.com", methods = {RequestMethod.GET, RequestMethod.POST})
public String getResource() {
//...
}
}
17. Explain session-based authentication?
Session-based authentication is a commonly used method to manage user authentication in web applications. It involves the use of sessions and cookies to maintain the authentication state and identify authenticated users.
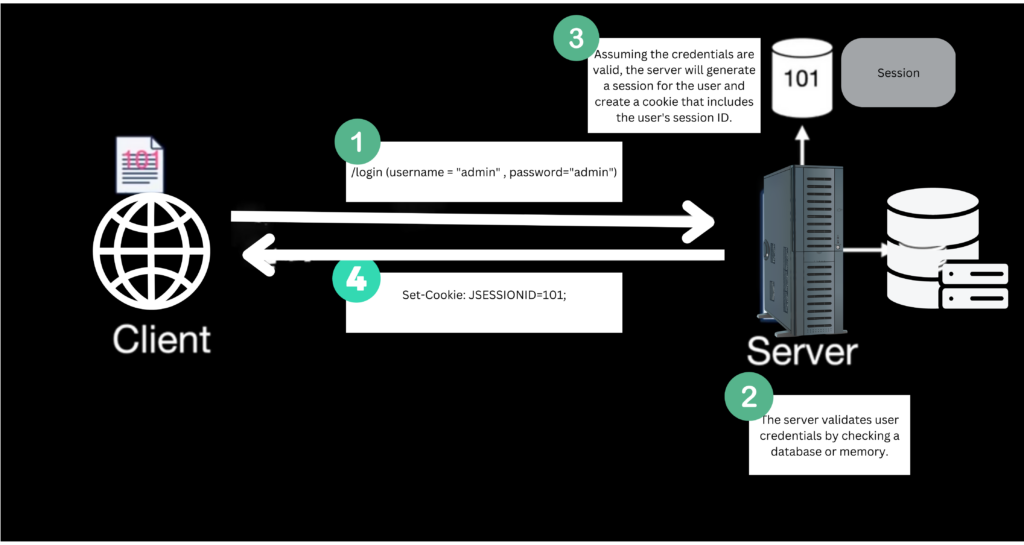
Here’s how session-based authentication works:
- User Authentication: When a user logs in to the application with valid credentials, the server verifies the credentials and creates a new session for the user. The session typically consists of a unique session ID.
- Session Creation: The server stores the user’s session ID in a session store (such as memory or a database) and associates it with the user’s authentication details and any relevant session data (e.g., user roles, permissions).
- Session ID Storage: The server sends the session ID back to the client as a cookie or as part of the response payload. The client’s web browser stores this session ID.
- Subsequent Requests: The client’s web browser automatically includes the session ID in the request headers (typically as a cookie) for subsequent requests. This allows the server to identify the user’s session and retrieve the associated authentication details.
- Session Validation: Upon receiving a request, the server validates the session ID to ensure its authenticity and integrity. It checks if the session exists and is still valid (e.g., not expired or invalidated). If the session is valid, the server considers the user authenticated and proceeds with the request.
- Session Expiration: Sessions typically have an expiration time to ensure security and manage server resources. Once a session expires, the user needs to re-authenticate by logging in again.
- Logout: When a user logs out, the server invalidates the session by removing it from the session store. The client’s web browser also deletes the session ID cookie.
18. How to prevent brute-force attacks?
Preventing brute-force attacks involves implementing measures that make it difficult for an attacker to guess valid credentials through repeated login attempts.
Here are some strategies we can employ to mitigate the risk of brute-force attacks:
- Account Lockouts: Implement account lockout mechanisms to temporarily lock user accounts after a certain number of failed login attempts. This can deter attackers from continuously guessing passwords. Once an account is locked, users can be notified or given a means to unlock their account securely, such as through a password reset process or by contacting customer support.
- Rate Limiting: Apply rate-limiting techniques to restrict the number of login attempts within a specific time frame. This prevents attackers from making multiple login requests in rapid succession. Implementing rate limiting can help mitigate brute-force attacks by slowing down the attack process and making it less effective.
- CAPTCHA or reCAPTCHA: Integrate CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) or reCAPTCHA challenges into your login forms. These challenges require users to solve puzzles or enter characters displayed in distorted images, which helps ensure that login attempts are made by human users rather than automated scripts.
- Two-Factor Authentication (2FA): Implement two-factor authentication to add an extra layer of security. With 2FA, users are required to provide a second form of authentication, such as a unique code sent to their mobile device, in addition to their username and password. This greatly reduces the risk of successful brute-force attacks, even if the attacker manages to obtain valid credentials.
19. How to handle Logout in Spring Security?
In session-based authentication, logout involves destroying the session object and deleting the session cookie in the user’s browser. This can be achieved by configuring the HttpSecurity as follows:
http
// Other security configurations...
.logout()
.invalidateHttpSession(true) // Invalidate the user's HttpSession
.deleteCookies("JSESSIONID") // Remove the session cookie
.logoutSuccessUrl("/login?logout") // Redirect to the logout success URL
.permitAll(); // Allow anyone to access the logout URLInterview Questions on Real Life Use-cases
20. How to support multiple password encoders during migrations?
To support multiple password encoders during migrations in Spring Security, you can use the DelegatingPasswordEncoder provided by Spring Security. The DelegatingPasswordEncoder allows you to configure multiple password encoders and associates each encoder with an identifier or “id”.
@Bean
public PasswordEncoder passwordEncoder() {
Map<String, PasswordEncoder> encoders = new HashMap<>();
encoders.put("bcrypt", new BCryptPasswordEncoder());
encoders.put("custom", new CustomPasswordEncoder()); // Replace with your custom encoder
return new DelegatingPasswordEncoder("bcrypt", encoders);
}In the above example, we configure two password encoders:
BCryptPasswordEncoderCustomPasswordEncoder
The DelegatingPasswordEncoder is initialized with the default encoder id (“bcrypt“) and the map of encoders. During authentication, Spring Security will determine the appropriate encoder based on the encoded password’s prefix or the provided encoder id.
21. Best practices for securing a REST-API?
Implementing REST API security involves various considerations to protect the APIs from unauthorized access and ensure data integrity.
- Authentication: Implement a secure authentication mechanism to verify the identity of clients making API requests. Common approaches include token-based authentication (e.g., JWT), OAuth 2.0, or API keys. Choose an authentication method suitable for the application’s requirements and integrate it into the API endpoints.
- Authorization: Define access control rules to determine what actions or resources each authenticated client can access. Use role-based or permission-based authorization mechanisms to enforce restrictions on API endpoints. Spring Security provides annotations like
@PreAuthorizeor@RolesAllowedto configure authorization rules at the method or endpoint level. - Secure Transport Layer: Ensure secure communication between clients and the API server by enforcing HTTPS. This encrypts the data exchanged between the client and server, protecting it from eavesdropping and tampering. Configure your server to use SSL/TLS certificates and enable HTTPS for all API endpoints.
- Input Validation: Validate and sanitize user input to prevent common security vulnerabilities like SQL injection, cross-site scripting (XSS), or other injection attacks. Apply input validation techniques and frameworks to sanitize and validate user-supplied data to mitigate the risk of security exploits.
- Rate Limiting: Implement rate-limiting mechanisms to protect against abuse and ensure fair usage of your API resources. Define limits on the number of requests allowed per client or per API endpoint within a specific time period. This helps prevent DoS (Denial of Service) attacks and ensures the availability and performance of your API.
- Logging and Monitoring: Logging and monitoring help in debugging on rainy days when we have to troubleshoot non-obvious and hard-to-reproduce issues.
22. How does Spring Security work with Mobile App Security?
Spring Security enables seamless integration with mobile application security, offering robust authentication and authorization capabilities.
One popular approach is token-based security, where mobile apps send authentication requests to a server and obtain a token (e.g. JWT) as the response. Subsequently, this token is included in all subsequent API requests to serve as the authorization mechanism.
Conclusion
This comprehensive guide of common Spring Security interview questions and answers explores key concepts such as authentication, authorization, and various components of Spring Security. We delved into topics like password encoding, request matching, method security annotations, and integrations with other frameworks. By familiarizing yourself with these interview questions and their answers, you can confidently tackle Spring Security-related discussions during interviews.
Happy Learning !!


Comments